.
The ctys-VMW plugin defines a meta-layer for an abstract interface, which is in current version based on the final commandline call of the supported products. The ctys-VMW plugin supports a subset of the products native command line options mapped to the ctys call options, the remaining are bypassed as native options. Future versions are going to provide an abstract encapsulation layer by a common ctys-wrapper script and in addition utilization of the vendor provided management interfaces for batch-mode installation and operations.
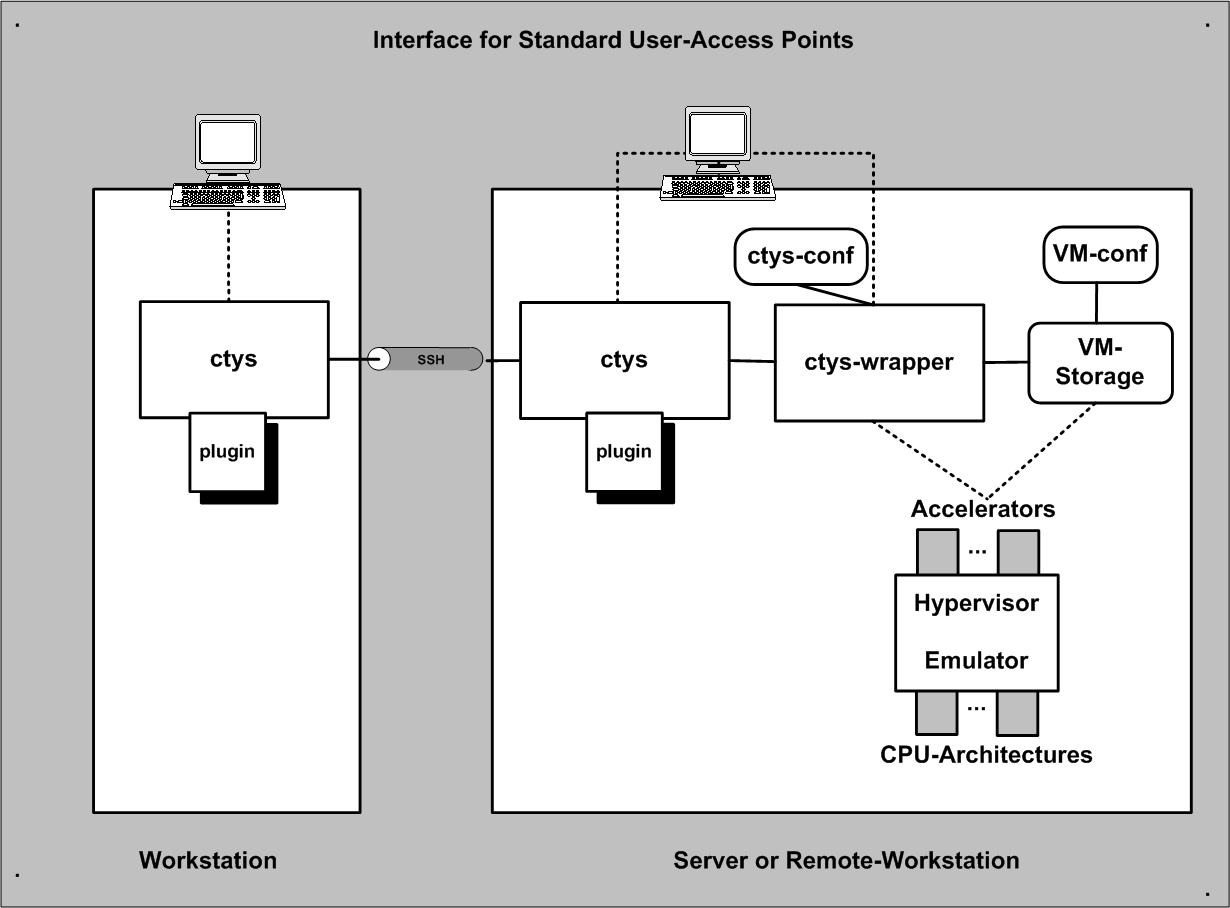
The call structure fits into the common structure of ctys but for the current version the
ctys-wrapper script is not yet supported for the VMW subsystem.

| Interfaces for Access Points |
|---|
The VMW subsystem supports the standard configuration files created by the vendor
utilities.
Thus any existing installation with any already present VMs and vmx-files could be used without
required adaptation.
These could be either used by dynamic addressing, dynamic search, or by unmodified scan into the inventory database.
The creation of new VMs is foreseen by the standandard procedures as defined by the vendor and supported
by the products.
The lack of the standard vmx-files is the missing of offline information about the GuestOS. The UnifiedSessionsManager provides for basically two options for the coallocated storage of additional extended GuestOS information.
The ctys-configuration-file is defined by convention to be stored within the directory of the virtual machine, coallocated with the vmx-file and named with the same prefix as the vmx-file: <vmx-file-prefix>.ctys and the containing directory ..../<vmx-file-prefix>. Even though this probably could varied, this has to be avaoided due to probable unanounced remove of the required features. The file could be created and added manually by the user with the same following optional "ctys-conf" vmx-file modifications and by the previous naming convention.
Alternatively the keywords could be stored within the vmx-file, due to the key-prefixes defined to begin
with a valid vmx-comment character these are protected for unintended evaluation by the hypervisor.
The provided example may suffice the most required offline information for the user-management
of the VM, including the automated generation of a cache database for the network inventory.
#@#MAGICID-VMW #@#VMSTATE="ACTIVE" #@#SERNO="20080415051600" #@#VERSION="01.01.001" ####MAC0 is provided by the eth0 of vmx-file! #@#IP0="192.168.1.235" #@#DIST="CentOS" #@#DISTREL="5" #@#OS="Linux" #@#OSREL="2.6" #@#CATEGORY="VM"
The current version is supported by the interactive installer ctys-createConfVM(1) which creates an appropriate addon-configuration file. For examples of CentOS installation as GuestOS refer to ctys-uc-CentOS(7). Once VMW is setup, the boot of the VM could be performed by the CREATE action of ctys. Basic Use-Cases for application are contained within the document ctys-uc-VMW(7).
The VMW plugin is supported on all released runtime environments of the UnifiedSessionsManager where the products are available.
The native GuestOS support is the same as for the PMs and HOSTs plugins.
The whole set of available CPUs by Products is supported :
x86, AMD64, x86_64
Current version supports the commandline interfaces of the products.
The current version supports for basic management facilities by a vendor provided tools. These comprise mainly the creation of runtime entities and the cancellation of running instances a.k.a sessions. Library functions for vendor provided coding interfaces are due to the lack of actual requiremtn not utilized yet. The interface for the commandline based tools varies between the producty and versions. The additional requirements such as a valid account with appropriate permissions including the actual call interface may vary, e.g. for vmrun between Server-1.0.10 and Server-2.0.2. The following tools are utilized for now as required:
The Installation of VMware is quite forward. Only some minor pitfalls occur for specific configurations with NIC-bonding. When a bonding device is utilized on Linux the mode=6 is not supported, which is the ARP-negotiation of client and server machines. The success of the support could be easily checked when using a guest system and calling ping. The effect is the lost of about the half of the ping-answers. This is somewhat a pity, because the mode=6 seems to be the fastest mode which even does not require support of intermediate network equipment. Any other mode seems to work properly.
The provided examples are based - if not stated else - on CentOS-5.4, but may be applicable for any other distribution similar.
The installation of VMware-Server(TM)-1.0.10 on CentOS-5.4
depends on the used kernel.
The description is verified to be applicable to linux-2.6.29.
The installation of VMware-Server(TM)-2.0.2 on CentOS-5.4 depends on the used kernel.
@include common-auth @include common-account
auth include system-auth account include system-auth
Install the rpm package VMware-player-1.0.5-56455.i386.rpm for the standard kernel linux-2.6.18-164.el5.
Install the rpm package VMware-player-1.0.5-56455.i386.rpm for the standard kernel linux-2.6.18-164.el5.
Install the bundle-package VMware-Player-3.0.1-227600.x86_64.bundle for the standard kernel linux-2.6.18-164.el5.
Install the bundle-package VMware-Workstation-6.5.3-185404.x86_64.bundle for the standard kernel linux-2.6.18-164.el5 and execute vmware-config.pl.
Install the bundle-package VMware-Workstation-Full-7.0.1-227600.x86_64.bundle* for the standard kernel linux-2.6.18-164.el5.
The most of the installation is performed with PXE if possible. Therefore the PXELINUX is switched to version 3.6.2 and a menu system for the management of the whole test-environment is setup. When difficulties occur due to specific network requirement, the CD-mount on ISO files option is used, which is almost in any case experienced to be quite safe for VMware products.
For initial creation or basic maintenance the console of the specific product has to be started.
The following options are available.
| Product | Version | Available Console |
|---|---|---|
| Server | 1.x | Proprietary |
| Server | 2.x | Browser, VMWRC |
| Workstation | x | Proprietary, VNC |
| Player | - | - |
| Overview of product specific consoles |
|---|
The console could be started e.g. by usage of the X11 plugin. This is the case for the 2.x versions of the Server-Products.
ctys -t x11 \
-a create=l:vmware,cmd:firefox%http:://127.0.0.1::8222 \
delphi
The double column masks this character as a native to be bypassed, else
it would be interpreted as a seperator of subarguments.
The non-SSL port is required in some cases, where the other is not operable.
Any X11 program could be executed, e.g. the proprietary console by:
ctys -t x11 \
-a create=l:vmware,cmd:vmware \
delphi
ctys -t x11 \
-a create=l:vmware,cmd:firefox%http:://127.0.0.1::8222 \
delphi
ctys -t vmw \
-a create=l:debian-5.0.0,console:vmwrc,user:acue,\
p:/mntn/vmpool/vmpool01/vmw/templates/debian-5.0.0 \
delphi
The folowing steps are applied to an installation by PXE. This anyhow requires the proper setup of DHCP, TFTP, and one of HTTP/FTP/NFS. For some OSs a so calld kickstart file could be used to automate the whole procedure.
For Linux and BSD refer to SYSLINUX and ETHERBOOT.
#@#MAGICID-VMW #@#VMSTATE="ACTIVE" #@#SERNO="20080415051600" #@#VERSION="01.01.001" ####MAC0 is provided by the eth0 of vmx-file! #@#IP0="192.168.1.235" #@#DIST="CentOS" #@#DISTREL="5" #@#OS="Linux" #@#OSREL="2.6" #@#CATEGORY="VM"
ctys -t vmw \
-a create=p:$HOME/vmware/tst-ctys/tst116/tst116.vmx,reuse \
-c off \
-C off \
host1
The install procedure for usage of an ISO-Image is almos the same as for PXE, just a few formal differences apply.
The remote console plugin of the Server-2.0 versions could be started standalone too, thus integrates seamless as a graphic terminal into ctys.
The compressed plugin for various architectures is stored in the directory:
/usr/lib/vmware/webAccess/tomcat/apache-tomcat-6.0.16/webapps/ui/plugin
This directory contains the files:
When calling ctys with the console type VMWRC now it should be considered whether the password will be provided by commandline or inserted into the dialogue mask when omitting. An alternative is the Single-Sign-On configuration.
The resulting call could be :
ctys -t vmw \
-a create=l:tst502,reuse,user:root%tst,console:vmwrc \
-c local root@lab02
The current version relies on the provided intstall mechanisms of the product supplier, and pre-requires an installed system.
debian-installer/allow_unauthenticated=true
Refer to the example in chapter "Installation and Maintenance by Product Console".
Installation is quite straight-forward and very similar to CentOS.
Installed from ISO image.
Installed from ISO image.
Installation is quite straight-forward, just the two-level boot has to be considered.
Installation is quite straight-forward.
| OS | name | Inst-VM | Media |
|---|---|---|---|
| CentOS-5.0 | tst117 | Server-1.x, 2.x | PXE,ISO |
| CentOS-5.1 | tst112 | Server-1.0.4 | PXE,ISO |
| CentOS-5.2 | tstxxx | Server-1.0.4 | PXE,ISO |
| CentOS-5.3 | tstxxx | Server-1.0.4 | PXE,ISO |
| CentOS-5.4 | tst131 | Server-1.0.10, 2.0.2 | PXE,ISO |
| CentOS-5.5 | x | Server-2.0.2 | PXE,ISO |
| Debian-4.0r3 | tst106 | Server-1.0.4 | PXE,ISO |
| Debian-5.0.0 | tst200 | Server-1.0.10 | PXE,ISO |
| Debian-5.0.0-amd64 | debian-5.0.0 | Server-2.0.2 | ISO |
| Fedora 8 | tst103 | Server-1.0.4 | PXE |
| Fedora 10 | tstxxx | Server-1.0.10 | ISO |
| Fedora 12 | tst201 | Server-1.0.10 | ISO |
| FreeBSD-7.1 | tst208 | Server-2.0.2 | ISO |
| FreeBSD-8.0 | tst209 | Server-2.0.2 | ISO |
| Gentoo-2009 | (tst231) | Server-2.0.2 | ISO |
| Mandriva-2010-free | tst227 | Server-2.0.2 | ISO |
| Mandriva-2010 | tst203 | Server-2.0.2 | ISO |
| OpenBSD-[2-4] | tstXYZ | WS5/6,Server-1.0.[1-5] | PXE,ISO |
| OpenBSD-4.0 | tst109 | Server-1.0.4 | PXE |
| OpenBSD-4.2 | tstxxx | Server-1.0.4 | PXE |
| OpenBSD-4.3 | tst155 | Server-1.0.4 | PXE |
| OpenBSD-4.6 | tst207 | Server-1.0.4 | PXE |
| ScientifiLinux-5.4.1 | tst204 | Server-1.0.10 | PXE,ISO |
| SuSE-9.3 | tst003 | WS6,Server-1.0.[345] | PXE,ISO |
| OpenSuSE-10.3 | tst116 | WS6,Server-1.0.[345] | PXE,ISO |
| OpenSuSE-11.2 | tst205 | WS6,Server-1.0.[345] | PXE,ISO |
| Solaris 10 | tst115 | WS6 | ISO |
| OpenSolaris 2009.6 | tst242 | Server-2.0.2 | ISO |
| Ubuntu-6.06.1-D | tst128 | Server-1.0.4 | ISO |
| Ubuntu-6.06.1-S | tst120 | Server-1.0.4 | PXE |
| Ubuntu-7.10-S | tst005 | Server-1.0.4 | PXE |
| Ubuntu-8.04-D | tst132 | Server-1.0.4 | ISO |
| Ubuntu-8.04-S | tst133 | Server-1.0.4 | PXE |
| Ubuntu-9.10-D | tst133 | Server-2.0.2 | ISO |
| Ubuntu-10.10-D | tstXYZ | Server-2.0.2 | ISO |
| MS-Windows-2000WS | tstXYZ | WS4/5/6,Server-1.0.[1-5] | PXE,ISO |
| MS-Windows-2000S | tstXYZ | WS4/5/6,Server-1.0.[1-5] | PXE,ISO |
| MS-Windows-2003S | x | Server-2.0.2 | ISO |
| MS-Windows-XP | tstXYZ | WS4/5/6,Server-1.0.10 | PXE,ISO |
| MS-Windows-NT-4.0S | tstXYZ | WS4/5/6,Server-1.0.[1-5] | PXE,ISO |
| Overview of Installed-VMs |
|---|
ctys(1) , ctys-createConfVM(1) , ctys-VMW(1) , ctys-uc-VMW(7) , ctys-plugins(1) , ctys-vhost(1) , vmware(1)
PXE-SYSLINUX-PXELINUX-ISOLINUX: <http://syslinux.zytor.com>,
PXE-ROM-Images-Etherboot: <http://www.etherboot.org>
Written and maintained by Arno-Can Uestuensoez:
| Maintenance: | <<acue_sf1 (a) users sourceforge net>> |
| Homepage: | <https://arnocan.wordpress.com> |
| Sourceforge.net: | <http://sourceforge.net/projects/ctys> |
| Project moved from Berlios.de to OSDN.net: | <https://osdn.net/projects/ctys> |
| Commercial: | <https://arnocan.wordpress.com> |
Copyright (C) 2008, 2009, 2010, 2011 Ingenieurbuero Arno-Can Uestuensoez
For BASE package following licenses apply,
This document is part of the DOC package,

For additional information refer to enclosed Releasenotes and License files.